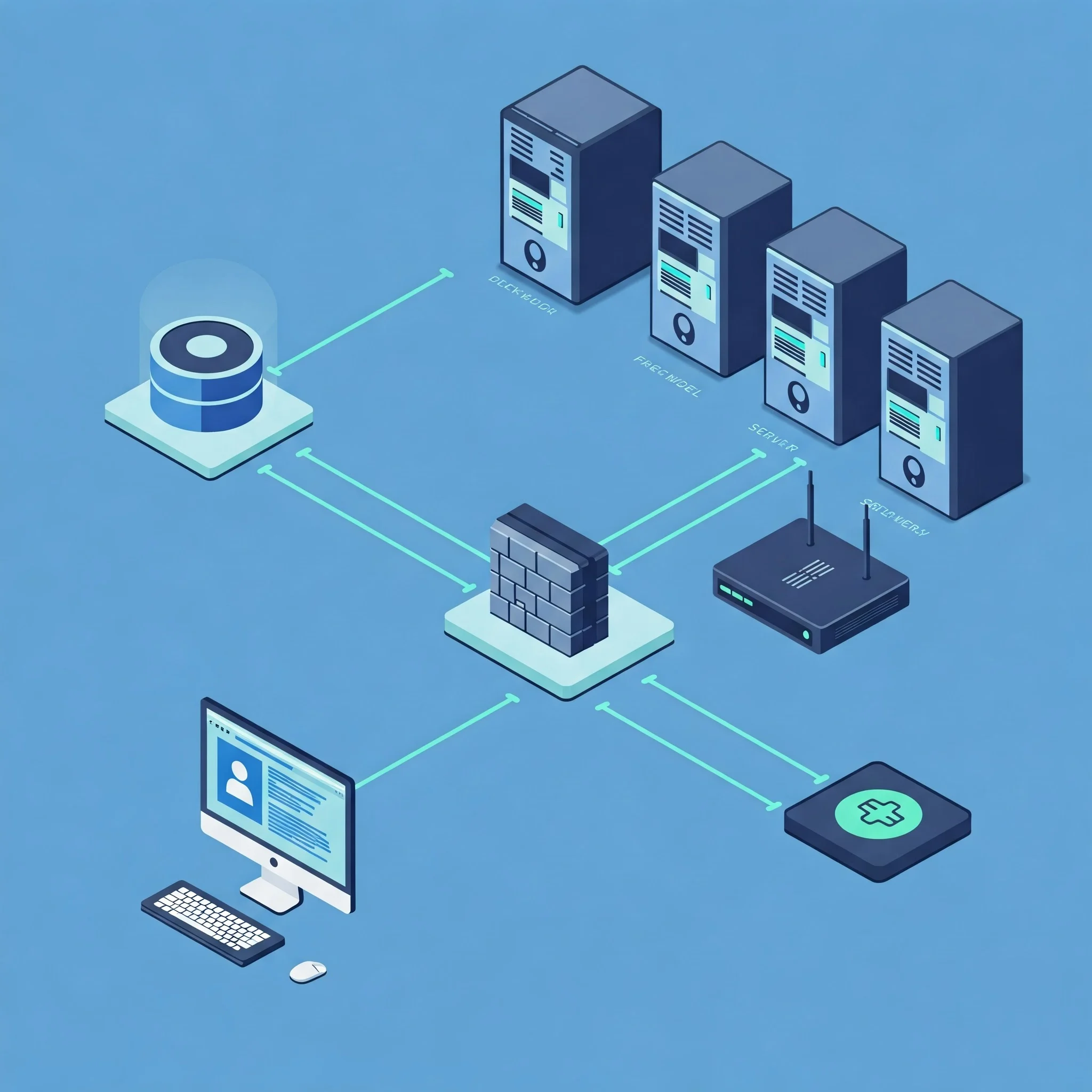
When you go to a website (like abc.com) or use your work computer, your information travels. It’s like an online journey with stops and safety checks. Let’s see how it works!

When You Visit a Website (External User):
Imagine you’re on your computer, ready to check out abc.com. Here’s the quick rundown of your data’s journey:
- You type in the address, and your request shoots out onto the Internet.
- It arrives at the organization’s digital front door: the Router. Think of it as the network’s address expert.
- The first security guard you meet is the Perimeter Firewall. This checks if your request looks legitimate. Lurking nearby is the IDS/IPS (Intrusion Detection/Prevention System), a silent watcher looking for any sneaky attempts to cause trouble.
- If all’s clear, you enter the public zone: the DMZ (Demilitarized Zone). Here, the Web Server lives, showing you the website’s public pages – the non-sensitive stuff. If there are multiple web servers, a Switch acts like a traffic director.
- Now, if you decide to log in, things get more secure. Your request now needs to pass through the Internal Firewall, a gatekeeper controlling access to the more private parts of the network. The IDS/IPS keeps an eye on this internal doorway too.
- You’ve reached the brain of the operation: the App Server in the secure Private Network. This server verifies your login (authentication) and decides what you’re allowed to see (authorization).
- To show you your personalized info, the App Server talks to the vault: the Database Server, also in the Private Network, where all the important data is stored.
- The information then travels back through the Internal Firewall to the Web Server, ready to be sent back to you.
- On its way out, it passes the Perimeter Firewall again, and finally, the Router sends it back across the Internet to your screen.
When an Employee Accesses Internal Tools:
Now, let’s see how an employee inside the organization gets things done:
- They start at their Employee Workstation, connected to the internal network.
- Their computer talks to a local Internal Switch, like a mini traffic controller in their office area.
- To reach other internal systems or the outside world, their traffic goes through the Internal Firewall, ensuring they’re following company security rules. The IDS/IPS monitors this internal flow.
- If they’re heading to a website, their traffic then goes through the Perimeter Firewall and the Router to reach the Internet. The IDS/IPS keeps a close watch here too.
- They can then access internal servers or external websites as needed.
- The information they request travels back along the same path, always under the watchful eye of the IDS/IPS.
The Silent Guardian: IDS/IPS
Throughout both these journeys, the IDS/IPS (Intrusion Detection/Prevention System) acts as a silent guardian. It’s constantly analyzing network traffic for anything suspicious. If it detects something odd (like an attempted attack), the IDS can alert the security team, and the IPS can even step in to block the threat automatically.
So, the next time you’re online or an employee is working, remember the intricate network pathways and the dedicated security measures in place to keep things running smoothly and safely!